Midland, Ontario Canada at the Wake of a Ransomware Attack
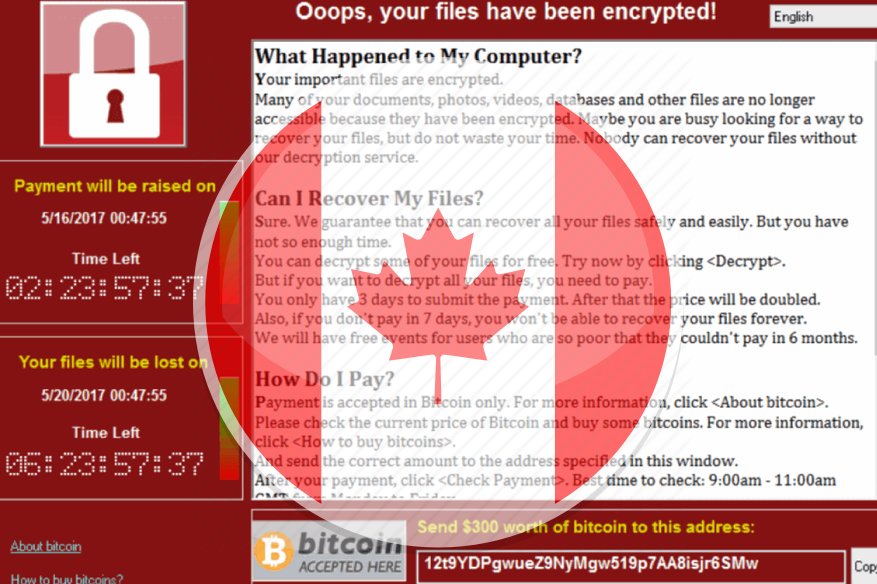
Ransomware is a very big business for cybercriminals when partnered with the victim’s inefficient or worse, non-existent backup system – that is a jackpot for ransomware authors. Ransomware attacks user’s data, encrypting them beyond recognition, and requires payment of ransom in order to decrypt them. Organizations and individuals that lack credible backup systems are at the worst end of a ransomware attack, as their only recourse is to nod, to pay the ransom to restore their critical data.
That story was what exactly happened in a 16,000-people size town in Ontario, Canada named Midland. The ransomware disabled the town’s computers last September 1, 2018, damaging financial processes and forced a shutdown of debit and credit card transactions. The Municipality’s vital data has been encrypted by the ransomware, without a credible backup solution prior to the ransomware attack.
The Midland municipal government has tapped their insurance provider, as such issue is covered by the latter. This, in essence, means that Midland paid the ransom in order to recover from their data loss. The municipal government has not disclosed how much was paid to the ransomware authors as of this writing.
It was a good decision for Midland to sign-up for an insurance policy for their data security, however, they severely lack the foresight to install an effective backup strategy. A credible backup system which can save them thousands if not millions of dollars in the event of a virus attack.
There is an unverified report that there was a spam email containing the ransomware that was accidentally opened by an employee. There is also speculation that Midland’s employees possess admin privilege with their computers, as the ransomware operates under the privilege of the logged-in user. The ransomware was able to take over the operations of the Midland’s PCs for the first 48-hours of the infection.
As of this time, classic channels such as junk commercial emails are still viable infection. It is very easy for busy people to lose attention to the risks involved with email, and many are very trusting to their email clients. It is very easy to get tricked by a spam email into clicking a malicious link or download the infected attachment.
Here are some of the safe computing methods to lessen the chance of a ransomware infection:
Backup Everything
It is essential that companies make regular routine backups with data stored offsite as there is currently no known way to decrypt the files affected by the malware.
Use Strong Passwords
Make sure you have a proper password policy in place for all user accounts with remote access – review all system accounts and delete any that are no longer required.
Consider disabling remote access
If you do not need remote access then consider disabling Remote Desktop or Terminal Services, close port 3389 or use IP based restrictions or a VPN.
Update Everything
Check the Microsoft Security Bulletins and ensure your systems are fully patched against known RDP vulnerabilities.
Alert others to prevent more attacks
Please forward this email to colleagues, friends, and family who could be impacted by a ransomware infection at their company.