Meet The New, Daring Version Of Matrix Ransomware

The remote desktop service had entered the mainstream consumer consciousness with Windows XP Professional, 17 years ago. This is to ease remote administration of Windows Desktop and Servers, without the need to purchase a separate program to do the job. It is always enabled by default on all Professional and Server editions of Windows, by opening TCP port 3389 and UDP port 3389.
However, when unused, an open Remote Desktop Service widens the attack surface of the system. This enables cybercriminals to find ways to take advantage of the opening for their own selfish interest. A new ransomware variant of “Matrix” has been revealed, taking advantage of the open Remote Desktop Service and connecting to its command and control server using the TCP port 3389 and UDP port 3389.
The new Matrix variant has a capability to scan IPs looking for any listening RDP service, it will then attempt a brute force remote desktop session. A successful penetration in effect encrypts all user files with a.FOX extension, lucky the algorithm of encrypting user files is very disk intensive, users will find it suspicious why the hard drive is very active, while no user-initiated demanding task is being processed by the computer.
Learn how to protect yourself from ransomware here.
The ransomware will a file named #FOX_README$.rtf, which directs the user to contact the virus author and inquire about the ransom payment process. The malware authors provided three email addresses for which the user can contact: FoxHelp@tutanota.com, PabFox@protonmail.com, and FoxHelp@cock.li.
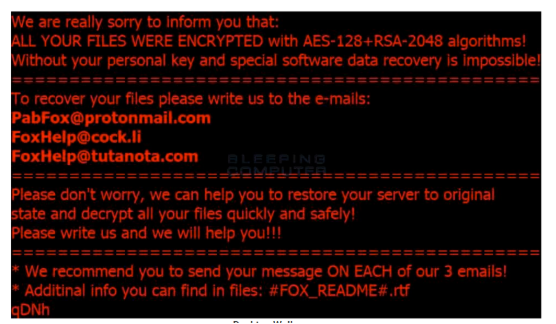
There is no way for the user to ignore the demand for ransom, as the Windows Desktop Wallpaper is also hijacked to display the below image:
The Malware authors also included in the ransomware payload the capability of Matrix to remove Volume Shadow copies of the files. This effectively cancels the possibility of restoring the encrypted files using the Volume Shadow back facility of Windows. But as mentioned earlier, due to the slow encryption process, force shutdown of the computer by pulling the plug can halt the encryption. When this is done fast enough, only a partial part of the hard drive is encrypted, enabling other files to still be accessible if the hard disk is connected with other computers.
It is highly recommended for IT teams to perform an internal audit, as not all PCs need to have an open Remote Desktop Service. This will help lock down the system, as removing RDP service means a smaller attack surface for hackers to exploit. People are also recommended to use an antivirus product with a built-in heuristics scanning, such antivirus programs have a higher risk of false positive, but they help fight unknown malware.
The success of ransomware today is anchored by the lack of reliable and efficient backup system. It is unfortunate, given that the market is flooded by competing for cloud-backup and cloud-storage solutions ranging from cheap service to completely free cloud storage SKU. An encrypted hard drive can easily be recovered with having a reliable backup solution, as a reformat+reimage+data restore from the backup is an effective method in reversing the damage caused by ransomware.