Why Disable SSDP/UPnP In Today’s Home And Enterprises?

When Did UPnP and SSDP Became Mainstream?
Universal Plug and Play (UPnP) was considered revolutionary when it was introduced to Windows Millennium Edition nineteen years ago, in 2000. It was hyped with the promise of automatic detection of ‘smart’ appliances in the home and in the office using a Windows PC. It is the pre-IoT era, where industries and people were starting to re-imagine what is it like for ordinary household appliance to be connected online.
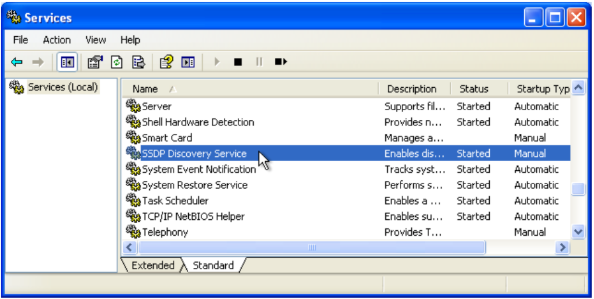
SSDP Discovery Service
This is when Microsoft thought the idea of creating a special service in Windows, the SSDP Discovery Service and retrofit it to the aging DOS-based code of Windows Millennium Edition.
The result was not only lackluster but rather a nightmare as Windows became more vulnerable to cyber attacks, as SSDP (Simple Service Discovery Protocol) and the UPnP system built-in to Windows is just another attack surface against the Microsoft operating system.
With Windows 2000, UPnP was introduced to the NT-based Windows branch, and that continued to this day. Unless disabled explicitly by the user using Services.msc, SSPD service that carries the UPnP feature by default.
What are the other uses of SSDP service?
SSDP is also used for inexpensive network compliant devices introduced in general households, general users who are not familiar with the technology leave them inappropriately set or leave as enabled. Especially devices for gaming such as PlayStation and, they detect if the network is UPnP-supported and automatically configures itself without manual human intervention.
Hence, whether the local network has a connected UPnP appliance or not the service is exposed on the network and continue to listen. This can be taken advantage of by cybercriminals that are scanning the Internet for Windows PCs with exposed UPnP service. The vulnerability without updating the software is real, as a stack like UPnP requires constant patching. An open UPnP port without an actual UPnP hardware is an opening anyone with enough knowledge to conduct an SSDP DDoS attack without the user able to detect the activity.
Why SSDP service is vulnerable?
One such attacks against UPnP is SSDP DDoS attack using reflection method is an exploit that puts a load by sending an inquiry that disguised an attack target as a transmission source to the device and sending the response back to the attack target. As SSDP returns a response that is about 30 times as large as the inquiry, it is more efficient to send a large amount of data the target by misusing corresponding devices rather than directly transmitting data to attack targets. Most attacks are done from port 1900 used by SSDP, with clever threat actors using a malicious payload was from a randomized port. The attacks originating from irregular port numbers are very difficult to the blacklist; it forces system administrators to do guesswork of what port to block and what port to allow out of 65,000+ available ports.
What can be done to prevent being compromised?
Disable the SSDP service from Windows and from the network, if the LAN has a connected PlayStation or Xbox deal with the manual configuration. Configuring port forwarding is not easy, but it is also not rocket science. Anyone with the desire to learn how to configure network devices without UPnP can do it, as the Internet contains many guides on how to configure port-forwarding. PlayStation and Xbox can also be security hardened by not depending on UPnP, as the port forwarding configurations are set in the home router, hence the complexity of configuration only has to happen once.