If you remember in September 2018, we came across a report from Nightwatch Cybersecurity regarding a security vulnerability in Android that allowed malicious apps to bypass permissions checks, and as…
Read More
Dependency on Android devices is increasing across the globe. Invariable of the country and size, millions of users store hundreds of significant personal and professional data on mobile devices. There…
Read More

According to Twitter, a bug that revealed the user’s location information, and shared it with an unnamed Twitter partner has been fixed. “We have discovered that we inadvertently collect and…
Read More
In a previous article we wrote here in Hackercombat.com, we have emphasized the need to change user’s perception regarding smartphones. It is not just a phone, but rather the ‘personal…
Read More
Google Android is a widely used operating system for mobile devices, in fact, it has even surpassed Microsoft Windows as the most used operating system across all computing devices. What…
Read More
At least 4 million Android users have reportedly got their devices infected with malicious beauty camera apps that are downloaded from Google play and which could steal personal pictures. Security…
Read More
Our mobile devices contain a lot of personal information, even more than on our computers. We go all day with our mobile phone, we can not leave home without it,…
Read More
Google has removed 85 Android apps from the official Play Store after it was reported that these apps were adware-infected. Google took the decision to suspend the apps after researchers…
Read More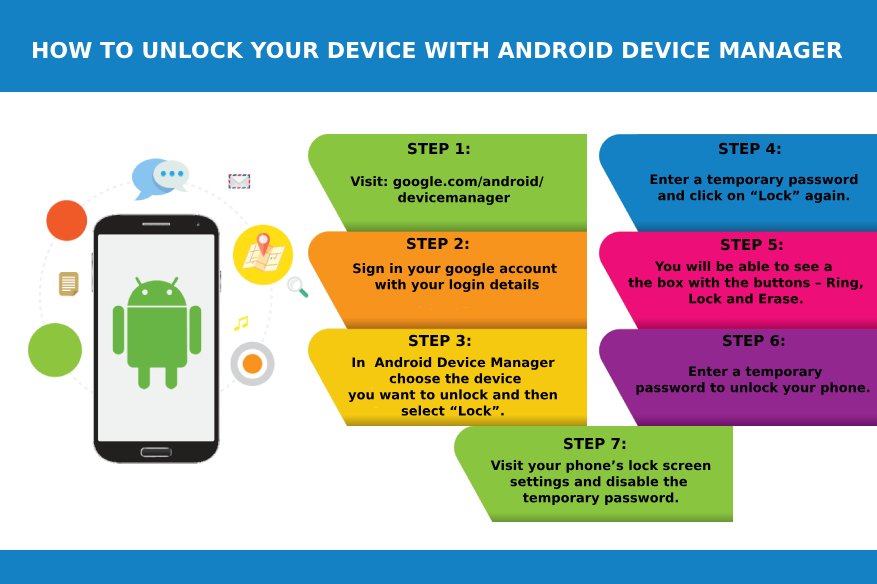
Android Device Manager – Android owns a tool that helps you to locate and remotely wipe your stolen device. Device Manager Device Manager is an applet in your operating System’s…
Read More
Apple’s iOS platform has been touted as a better mobile OS than Android in the standpoint of security. However, contrary to the loyal followers of Apple, their hardware and their…
Read More