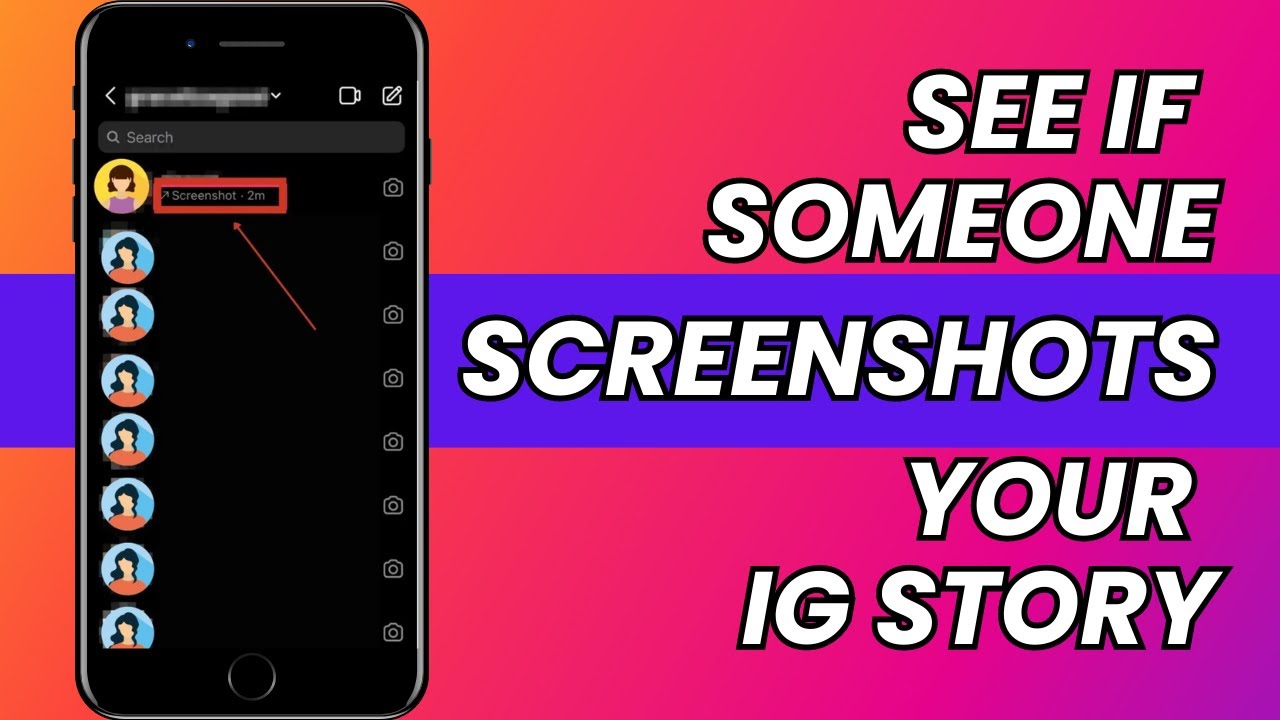
A Closer Look At Simple Signs That A Is Possibly Smartphone Is Infected
In a previous article we wrote here in Hackercombat.com, we have emphasized the need to change user’s perception regarding smartphones. It is not just a phone, but rather the ‘personal…
Read More