Massive Malvertising in Chrome iOS Variant, Caused By eGobbler Group

The notorious eGobbler group has set its sight on the iOS version of Chrome browser, as they use the platform for malvertising. Also, known as Malicious advertising, malvertising is a deceptive action of a group to publish a certain advert on a website, but instead of directing the user to the publisher of the advert, it points them to a malicious website instead. In the case of Chrome for iOS, eGobbler group was able to hijack some genuine advert servers, which then delivers a certain number of malformed adverts that redirects visitors to a scam/phishing website instead.
Confiant, a cybersecurity consulting firm, confirmed that at least 500 million malicious ads had already displayed itself inside a Chrome for iOS browser in the first 10 days. eGobbler’s motivation for the campaign is very clear, earn a profit. An additional profit stream for eGobbler may come from advert-supported landing pages and through covert user data collection.
Unlike the Chrome browser in Windows, Linux, MacOS and in Android, the iOS version of Chrome uses Apple’s Webkit engine instead of the Google-developed Blink. This behavior is by design, as Apple devices cannot run other browser engines other than Webkit, which severely limits other browser vendors in providing a leveled feature set of their browsers across platforms.
Further, checking revealed that the exploit only affects Chrome for iOS, as the exact condition that can trigger the malvertising is only executable and hardcoded in the iOS platform. Confiant provided an example below on how eGobbler customized its message in order to make itself persuasive:
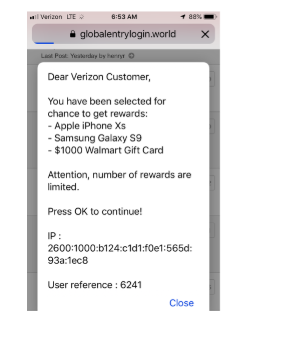
“Like other bad actors, eGobbler leverages cloaking techniques and obfuscation to make their payloads look like legitimate ads, but a closer look at the payload behind these recent attacks reveals a very special twist. We were already aware from our internal blocking metrics that the campaign is iOS targeted. Normally this would not be alarming, as this is common among malvertisers for varying reasons. However, given the volume of this attack we decided to inspect it with extra scrutiny,” emphasized Eliya Stein, Confiant’s Sr. Security Engineer.
This can happen through the use of browser session hijacking, a technique used in order to force a web browser to immediately open a website that the users themselves never intended to open just because an unrelated link was clicked. This is done through the use of a malformed JavaScript which tells the browser to proceed to open another site (seemingly not related to the site the user visited) on another tab.
All modern browsers have a pop-up blocker, in fact, if we can remember, even the dreaded Internet Explorer 6.0 way back in the Windows XP days (circa 2001), Microsoft added a pop-up blocker in IE as part of Service Pack 2. However, the Chrome for iOS has a flaw in its detection mechanism of pop-ups, hence the pop-up blocker is bypassed, allowing the malvertising to be displayed uninterrupted.
“We tested the eGobbler payload against the standard set of sandboxing attributes as they exist in 90% of Google’s ad serving products. While on the surface the allow-popups directives seem like there’s nothing special about eGobbler’s payload, this is not true, because these actions should only be possible as a result of direct user interaction , a requirement that the eGobbler exploit successfully circumvents. The fact that this exploit is able to bypass that need for user interaction should be impossible according to the same-origin policy as it pertains to cross-origin iframes,” concluded Stein.
Source: https://www.forbes.com/sites/daveywinder/2019/04/17/iphone-users-under-attack-as-ios-chrome-security-sandbox-fails/#52457c9c2f43
Also, Read:
Android is Now as Secure as iOS!
New Google Chrome Zero-Day Vulnerability Detected
Google’s New Chrome Extension Seeks to Secure Accounts