Global Threat Statistics for the week of April 5, 2019

Cryptojacking Boosts Botnet Expansion
Botnets have been essential tools in distributed denial of service attacks for many years. With the continued success of DDoS attacks, it was only a matter of time before botnets were used for other malicious activities. In the past year, we’ve seen botnets used for generating spam and phishing emails, DNS attacks, pay-per-click abuse, ransomware, and cryptojacking.
Cryptojacking, in particular, has seen a significant increase. BleepingComputer just reported on a cryptojacking botnet that is actively attacking Asian targets. The same cryptojacking campaign was detected attacking Chinese targets back in January. Among other attempts to compromise its targets, the attack deploys a malicious XMRig Monero crypto miner.
These botnets can be massive. The Necurs botnet is comprised of 570,000 hosts (more specifically, unique bot IDs) according to Century Link’s Black Lotus Labs. Among them, India leads the pack, hosting nearly one in five Necurs bots.
The statistics that follow are based on an analysis of over 100 million endpoints by Comodo Threat Intelligence Lab for the week of April 5, 2019. In addition to botnets, it includes statistics on malware and phishing.
Countries and Regions Hosting and Malware Botnets
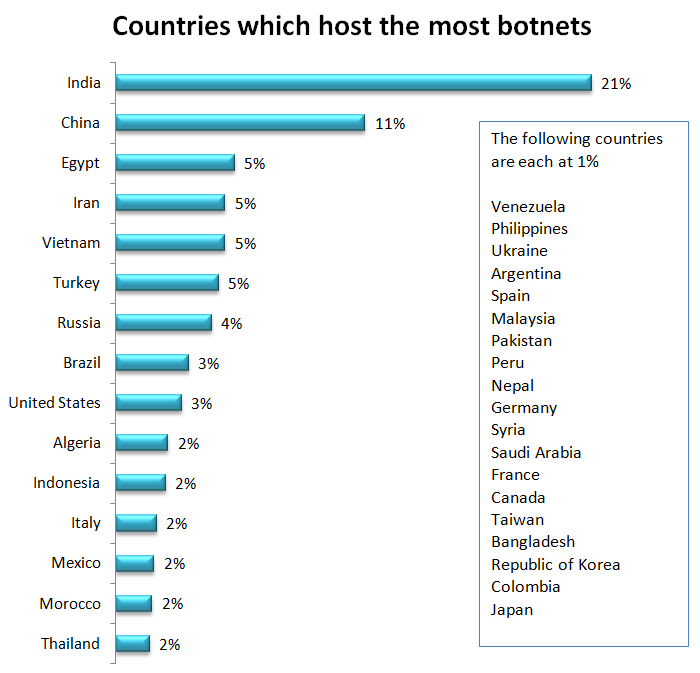
With active botnets like Necurs and others targeting computers in India and China, it is understandable that those two countries account for one-third of all botnets, with India at 21% and China at 11%. There are a number of variables that impact where malware and botnets may be hosted, such as availability of target computers, ease of access, the vulnerability of accessible computers, and type of malware. These are constantly changing, so it introduces a bit of randomness to the results, making the statistics that follow a snapshot in time.
Egypt, Iran, Vietnam, and Turkey account for 5% each. Russia follows at 4%, with Brazil and the United States close behind at 3%.
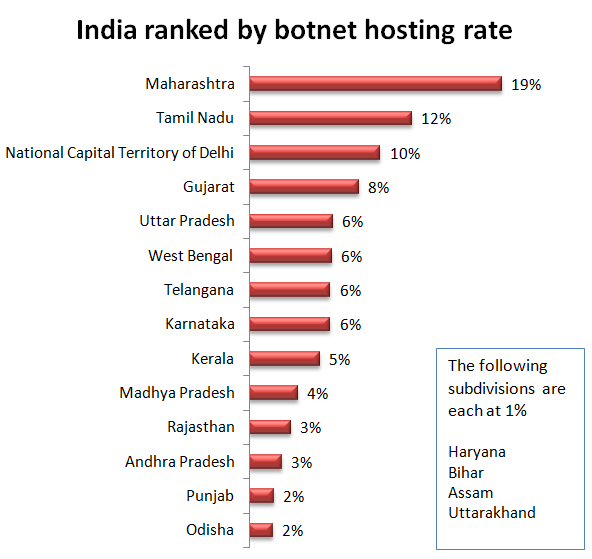
Within India, Maharashtra hosted 19% of botnets, followed by Tamil Nadu at 12%, National Capital Territory of Delhi at 10%, Gujarat 8%, and Uttar Pradesh, West Bengal, Telangana, and Karnataka at 6% each. Ten other regions each shared a small percentage of the remaining botnet hosts.
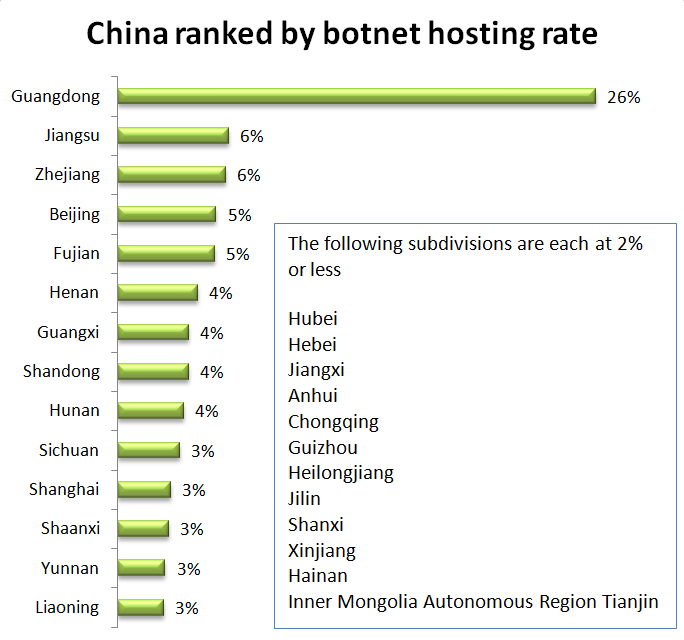
Within China, Guangdong hosted just over a quarter of botnets. Zhejiang and Jiangsu each hosted 6%. Beijing and Fujian each hosted 6%. Twenty-one other territories each hosted less than 5%.
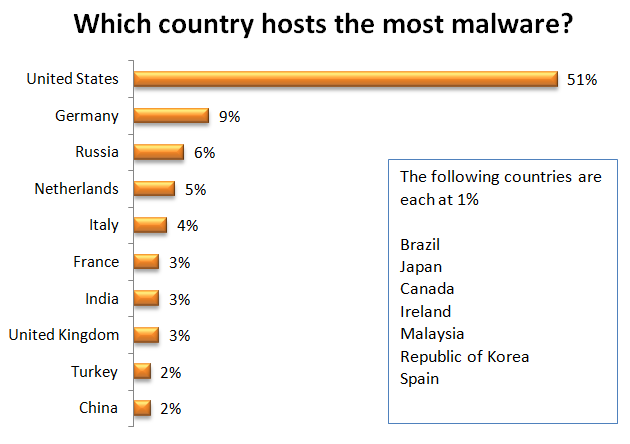
The United States hosted just over half of the world’s malware, down considerably from 63% in our last report. In the same time period, Germany jumped from 3% to 9%. Russia, Netherlands, and Italy follow with 6%, 5%, and 4%, respectively. France, India, and the United Kingdom are at 3% each, with all other countries listed each hosting 2% or less.
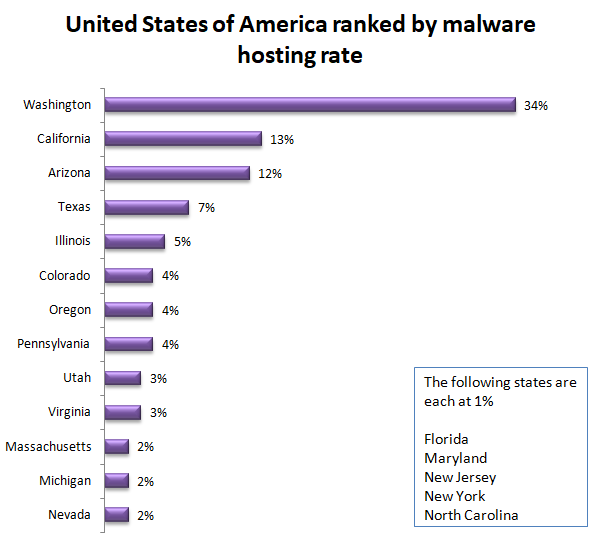
Within the United States, the west coast hosted just over half of the world’s malware with Washington at 34%, California at 13%, and Oregon at 4%. Washington had a significant drop since in our last report, from 79% to 34%. California more than doubled from 6% to 13%.
Arizona joins the list at 12%. Texas follows at 7%. Also joining the list is Illinois at 5%, Colorado and Pennsylvania, both at 4%, and Utah and Virginia, both at 3%.
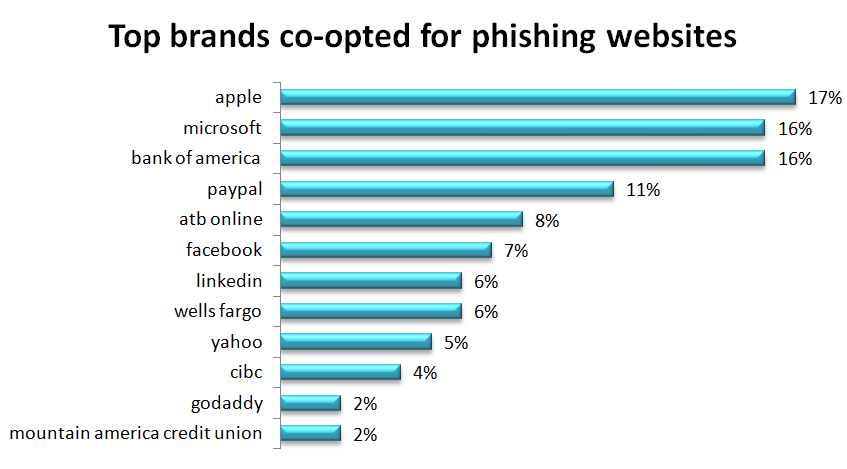
One of the most successful phishing methods is to co-opt a well-respected brand, so it is no surprise that impersonating Apple and Microsoft occurs in one-third of website co-opt attempts. The goal of a phishing attack using these brands is to access your computer or device. The phishing usually comes in the form of a pretext of Apple or Microsoft technical support claiming they will fix some horrible (but somehow symptomless) problem you have. The goal is to have the user give them remote access to “fix” the laptop. Once the access is granted, they install malware that will typically include a keystroke logger and other tools to send them useful information from the device.
Half of the brands on the list are financial institutions. These are popular for the same reason their brick-and-mortar peers – that’s where the money is. Facebook, LinkedIn, Yahoo, and GoDaddy are phishing targets for account takeover. Taking over a GoDaddy account may give a cybercriminal full control of a website from which to launch phishing attacks. Impersonation is the goal of taking over a Facebook, LinkedIn, or Yahoo account. The cybercriminal lures your contacts or connections by pretending to be someone they trust, you.
The scale at which these attacks are being deployed is evident in the number of web pages using this type of attack. This analysis discovered 210,560 web pages impersonating these brands for the purpose of phishing, considerably more than the 61,767 in our last report. Most of those have since been taken down but over 50,000 malicious web pages are still up and running to lure your users.
Sharing this information is important so that your users know to be more vigilant if they get an email or alert, supposedly from Apple, Microsoft, or the others in this chart. Some of these phishing websites look quite authentic and may fool even security-minded users. This type of information is a great addition to your security awareness program.