A cybercriminal who takes advantage of compromised credentials rather than having to hack a DNS server, warning a DNS expert, is what we call DNS-level attacks. This is getting popular…
Read MoreLeaks

Wireless LAN access points (hereinafter referred to as wireless APs) are highly convenient and are being installed for internal business purposes. However, there are three security threats in the wireless…
Read More

DNS protection provides an additional level of protection between the user and the Internet by creating a blacklist of malicious websites and filtering out unwanted content. By using a secure…
Read More
Scammers abuse the notifications and push APIs on Android devices to send spam alerts that are customized to look like a missed call. Both APIs are used on mobile devices…
Read More
As a long-promised feature of the digital age, artificial intelligence is finally making real strides into many aspects of mainstream security. From personal computing systems to vast online casino networks,…
Read More
According to ZDNet, a hacker by the name Gnosticplayers reveals to them in February about wanting to put up data of over one billion users for sale. ZDNet finds that…
Read More
The immensely popular VSDC multimedia editing software has reportedly been hacked and used to spread banking trojan. Reports say that users who have downloaded the VSDC editing software, which is…
Read More
Over the last few years, several gaming platform-based cyber attacks have come to light. Given the rise in microtransactions and in-game currency that is present in online multiplayer games and…
Read More
We have always been stating that for any enterprise, security is not just about solutions and the technical aspects, it includes the human element as well. Every single employee who…
Read More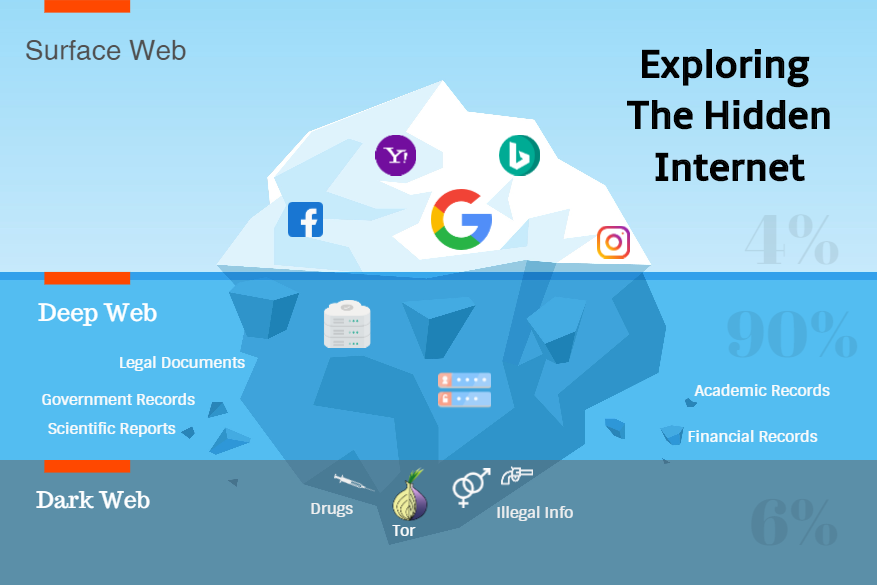
When we have to search for something on the Internet, our mind, by default, goes to Google or Bing. Our mind is tuned, and we get the results we seek….
Read More