iCloud can be an easy and secure way to back up photos and videos, but accessing those files across devices may prove challenging. Thank goodness there are multiple ways to…
Read MoreLeaks

If the iPhone force restart does not work as intended, there may be an issue with the iOS system. To address this, look for physical damage to buttons used for…
Read More

If the YouTube app on your iPhone is crashing or will not open, there are various fixes you can try, such as force quitting the app, rebooting your device, and…
Read More
Instagram is an amazing social platform where you can stay in touch with your friends and influencers, but sometimes it can be too much. Taking a break may help. Instagram…
Read More
An inactive Facebook business page won’t do your brand any good; sometimes, it may be best to delete it and start fresh. Deleting a page is straightforward and can be…
Read More
Get a simple solution for the question “Do AirPods Work With Android” – Yes, AirPods work well with Android, but the experience may be less satisfying or convenient compared to…
Read More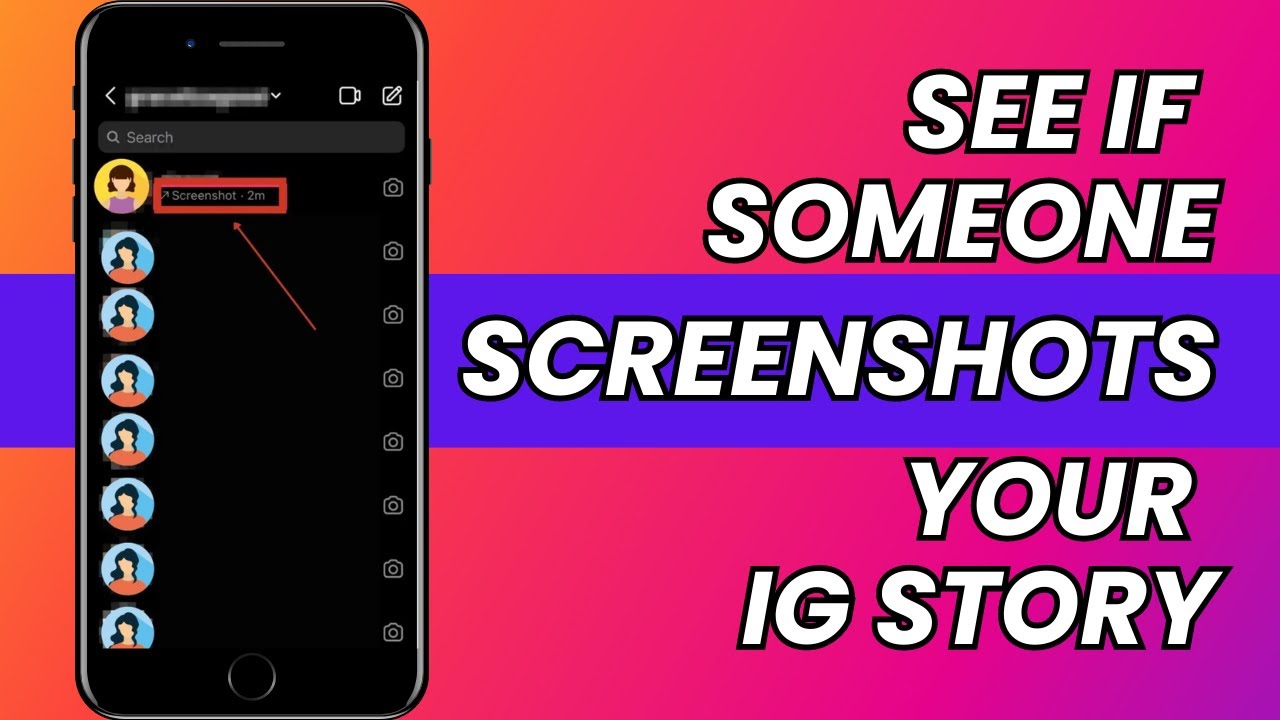
Instagram doesn’t inform its users when their Story or Reel has been screengrabbed – no matter whether they have millions of followers or just an everyday account – which means…
Read More
The iPhone offers multiple ways of scanning QR codes, but the quickest and easiest method is using its built-in camera app. Open your camera app and point at a QR…
Read More
Keep your AirPods protected when not in use by keeping them inside a waterproof charging case to protect them from falling into liquid environments such as puddles, sinks or other…
Read More
QR codes have become an indispensable feature of everyday life. From restaurant menus to bathroom stall doors, QR codes provide an easy link between offline and online experiences. Select between…
Read More