Cyber threats can wreak havoc on businesses, from data breaches to loss of reputation. Luckily, there are effective strategies available that can reduce cybersecurity risk. Avoidance is one of the…
Read MoreLeaks
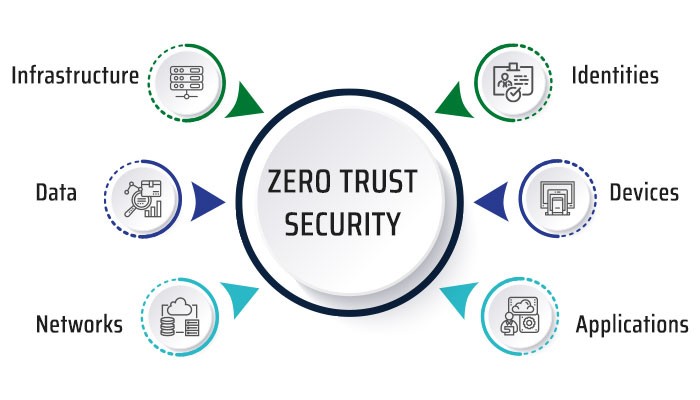
Zero trust security takes an “never trust, always verify” approach to access control. Access is only granted once an individual’s identity and context have been confirmed through multifactor authentication and…
Read More
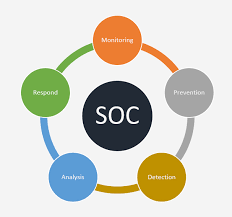
A Security Operations Center (SOC) specializes in monitoring and analyzing data to detect cyber threats and prevent attacks from them. They work to sort actual threats from false positives before…
Read More
Endpoint detection and response (EDR) tools offer businesses that employ hybrid work models or remote employees an extra layer of cybersecurity protection. Utilizing artificial intelligence (AI) and machine learning (ML),…
Read More
EDR can detect and respond to emerging and advanced cyber threats quickly and efficiently, making it an essential component of modern business ecosystems. Beyond signature-based detection capabilities, its features go…
Read More
Cloud security involves employing perimeter defenses like firewalls, IDPSs and VPNs as well as guaranteeing isolation through network segmentation and virtual LANs while monitoring traffic for anomalies and threats –…
Read More
Computer viruses are extremely hazardous, which is why it’s crucial to secure your devices with reliable malware removal programs. These free applications serve as your second line of defense against…
Read More
Malware refers to any form of malicious software which aims to disrupt, harm or steal private information for criminal use. Furthermore, malware can mine cryptocurrency for cybercriminals as an additional…
Read More
If your Excel file was left unsaved by accident, don’t fret – Microsoft understands mistakes happen and provides built-in functionality to help recover it. To recover an unsaved file, navigate…
Read More
If you suspect someone has blocked you on Facebook, various methods exist to investigate their actions. One option would be searching for their name; they may have blocked you if…
Read More