USB type-C ports and connectors are slowly but surely picking-up popularity, as it replaces USB-A and Micro-USB due to the strong influence of mobile computing. The speed of USB type-C…
Read MoreTech
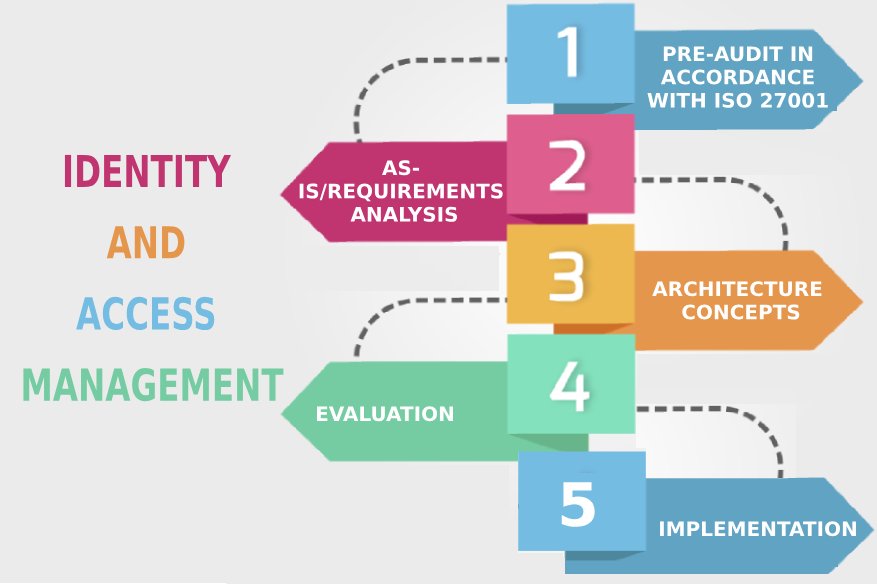
The tendency for companies to adopt consumer technologies (also known as commoditization) is increasing rapidly and that means a change in the operation and management of corporate environments and business…
Read More
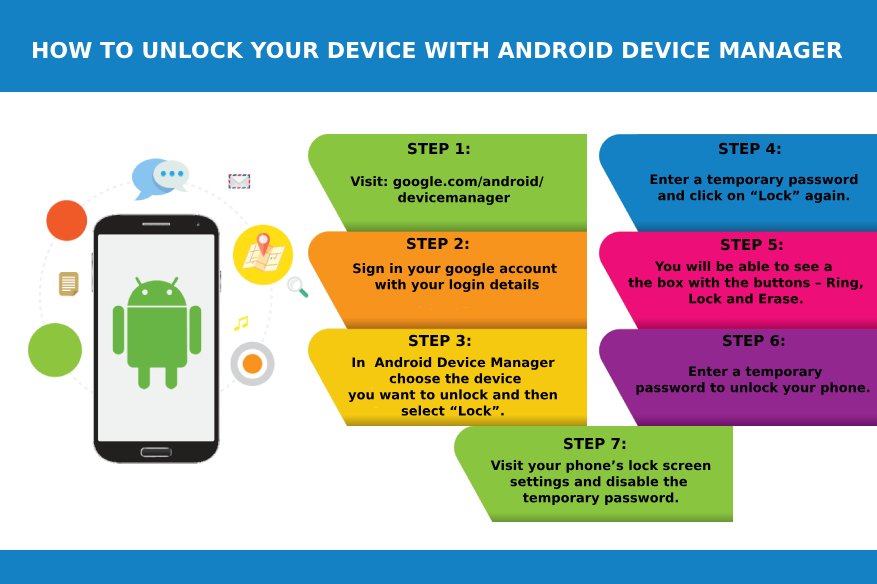
Android Device Manager – Android owns a tool that helps you to locate and remotely wipe your stolen device. Device Manager Device Manager is an applet in your operating System’s…
Read More
Domain-based Message Authentication, Reporting and Conformance (DMARC) is an anti email spoofing technology first drafted in 2012 to help address the issues of fake and phishing email messages. The system…
Read More
A security flaw in a GDPR-themed WordPress plugin has been used by hackers to hijack websites, as per reports. A blog post by Defiant, a company that focuses on WordPress…
Read More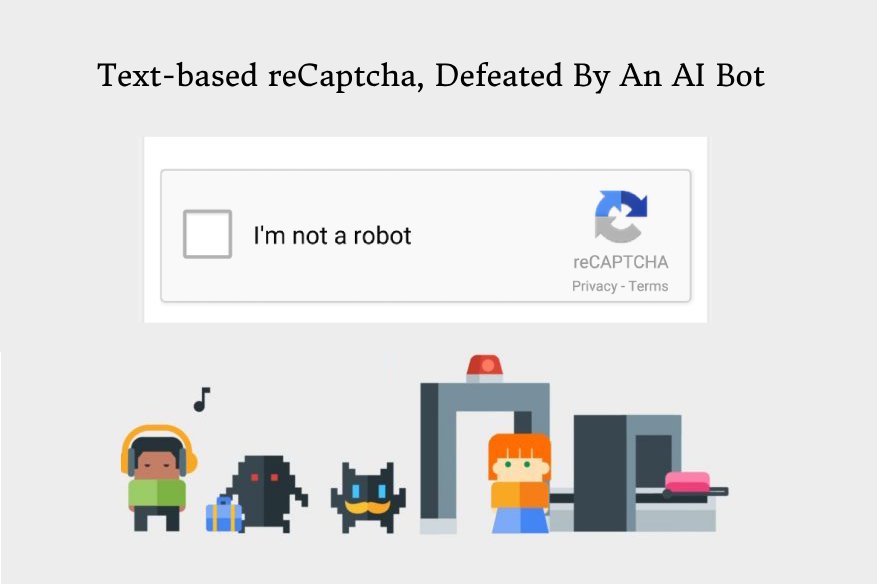
Anyone who browses the web is very familiar with the anti-robot technology we call CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), that blocks everyone to…
Read More
Companies today have largely accepted that technology is here to stay, and not embracing it is not in the table. The white flag has been raised, even for the strict…
Read More
YouTube now finally decides to remove its annotations feature, after having discontinued the annotations editor earlier. It was in May 2017 that Google discontinued the YouTube annotations editor, after finding…
Read More
Women in technology is a force to recon with, as it is one of the most gender-neutral industries on a global scale. This has been the message echoed in the…
Read More
Yes, really. Your government or a foreign spy agency might be tuning in right now through your router or your server equipment. Two Cases of Hardware Tampering In 2015, Amazon…
Read More