Threat actors want to maintain anonymity in their operations, especially in the art of virus development and phishing expedition. They continue to find ways to bypass detection, as mere suspicion…
Read MoreSecurity News

Obfuscation of Source Code of Phishing Messages Through Web Open Font Format, Growing in the Wild
- January 6, 2019
- by Julia Sowells
- 0
13 Privilege Escalation Bugs For CleanMyMac X Discovered, Updated Fix in Version 4.2.0 Released
- January 6, 2019
- by Kevin Jones
- 0
In the Windows platform, the use of system cleaning tools such as CCleaner has been a regular part used for Windows computer housekeeping. Same housekeeping is required with a Mac,…
Read More

New USB-C Technology for Better Protection Against Malware
- January 5, 2019
- by Julia Sowells
- 0
USB type-C ports and connectors are slowly but surely picking-up popularity, as it replaces USB-A and Micro-USB due to the strong influence of mobile computing. The speed of USB type-C…
Read More
The Universal Importance of IAM (Identity and Access Management) In A Firm
- January 3, 2019
- by Julia Sowells
- 0
The tendency for companies to adopt consumer technologies (also known as commoditization) is increasing rapidly and that means a change in the operation and management of corporate environments and business…
Read More
PayPal Block The Hacker News
- January 2, 2019
- by Kevin Jones
- 0
Well, Paypal just killed Hacker News, and does this means the beginning of the end. With thousands and thousands of followers on line, The Hacker News,” is a preferred cybersecurity…
Read More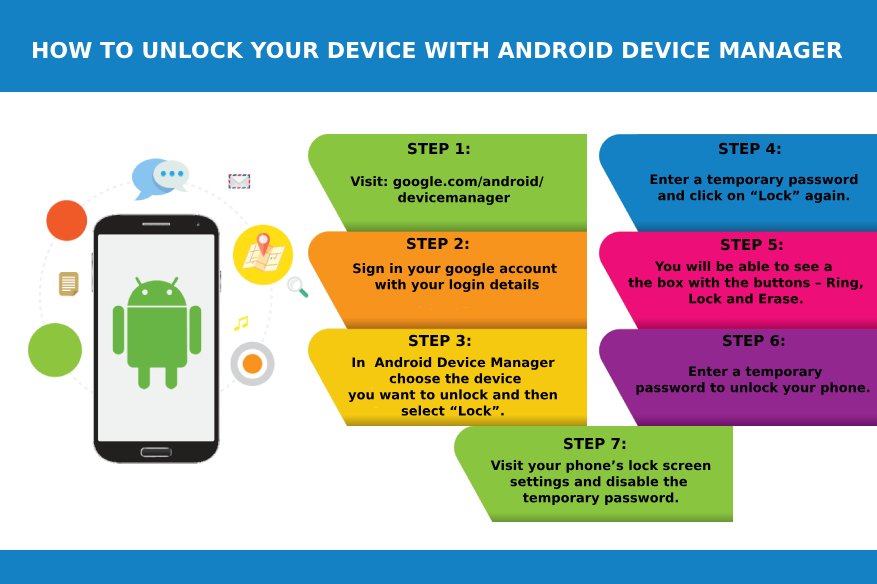
How to Unlock Your Android Device Using Android Device Manager?
- January 1, 2019
- by Kevin Jones
- 0
Android Device Manager – Android owns a tool that helps you to locate and remotely wipe your stolen device. Device Manager Device Manager is an applet in your operating System’s…
Read More
Facebook Collects Data of Non-Users via Android Apps
- December 31, 2018
- by Julia Sowells
- 0
If think Facebook is collecting data after you have gone through all that stories, and want to quit or already did it, then let you be confirmed that Facebook is…
Read More
Vigilante Hacker Hijacked Twitter Accounts To Prove Security Issue
- December 28, 2018
- by Julia Sowells
- 0
According to a report on the portal Independent, an online hacking security agency claims to have “hijacked” multiple Twitter accounts to prove their point how regarding online security issues. A…
Read More
4 Things Gamers Should Never Forget Even If It Is The Holiday Season
- December 28, 2018
- by Julia Sowells
- 0
As the holiday season continues, people have more time for their families and of course for computer gaming. PC gaming has evolved from a hobbyist activity to a full-blown sport…
Read More
Almost 19,500 Orange Modems Leaking WiFi Credentials
- December 24, 2018
- by Julia Sowells
- 0
This is becoming a real headache for customers of Orange Livebox ADSL modem in France and Spain during the Christmas season; almost 19,500 modems have been discovered leaking WiFi credentials….
Read More