Forensic investigations became the “new normal”, as cybercriminals increased their activities at the expense of users and businesses alike. It is sad to admit that cybercrime is set to grow…
Read MoreCyber Crime

TOR, also known as the Onion router has been the go-to method for the privacy-savvy people to browse the web with confidence, as TOR traffic hides people’s identity. However, browsing…
Read More

Australian statistics has revealed that 63 data breaches have been reported in the first two months of the year, which is something that needs to be addressed. Out of the…
Read More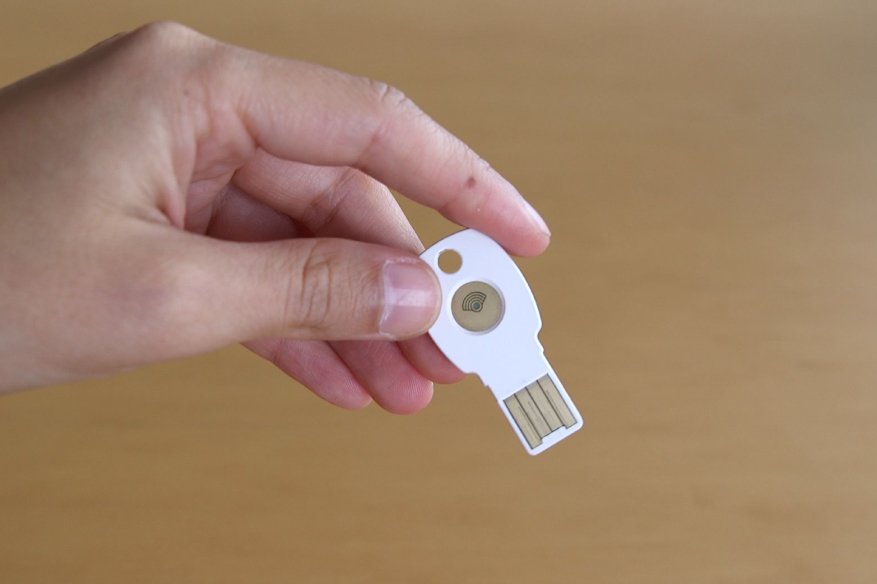
Google employees from the CEO to staff level developers have no history of getting phished, socially engineered or data breached. Not because all of them are the superhuman genius that…
Read More
Organizations should, in addition to preventing or combating cyberattacks themselves, also provide assistance to law enforcement agencies in combating cybercrime and tracking down cybercriminals. Unfortunately, this is an area that…
Read More
When it comes to Cybersecurity news, first world nations almost always take the center stage. When a breach happened in a Silicon Valley-based company, it is a dime-a-dozen for mass…
Read More
The Android platform is again in the cybersecurity news headlines this week, this time around with the persistent spread of BusyGasper spyware. According to Kaspersky Labs, BusyGasper has been in…
Read More
Malware authors and cybercriminals of today are after profit at the expense of legitimate businesses and individuals. A cyber attack is very different from a physical theft, as the damage…
Read More
Mimecast, a data security firm recently announced the result of their quarterly Email Security Risk Assessment report revealing an 80% increase of phishing, through the use of impersonation activities. In…
Read More
