Keeping sensitive data secure against theft and vulnerability should be a priority for most organizations. However, this isn’t as easy as it may seem especially with new technologies and evolving…
Read MoreData security

Yes, you read it right! Organizations in Singapore are struggling to cope up with the volume of software patches. According to new research released by ServiceNow, Inc has, this year…
Read More

Consumer watchdog says Google gathers and uses location data without telling users. The Australian Competition & Consumer Commission (ACCC) is bringing up against Google and its Australian branch claims of…
Read More
For PC manufacturing and silicon partners, Microsoft is collaborating to develop computers with a stable firmware layer. The project aims to counter threats targeting firmware and operating systems with the…
Read More
Why buy if you can use it for free? Instead of paying for premium services, why don’t you use a free VPN for Android? Many of these apps have similar…
Read More
You may be one of those individuals who can’t let a day pass without interacting with numerous applications and websites. Do you know that many of these sites and apps…
Read More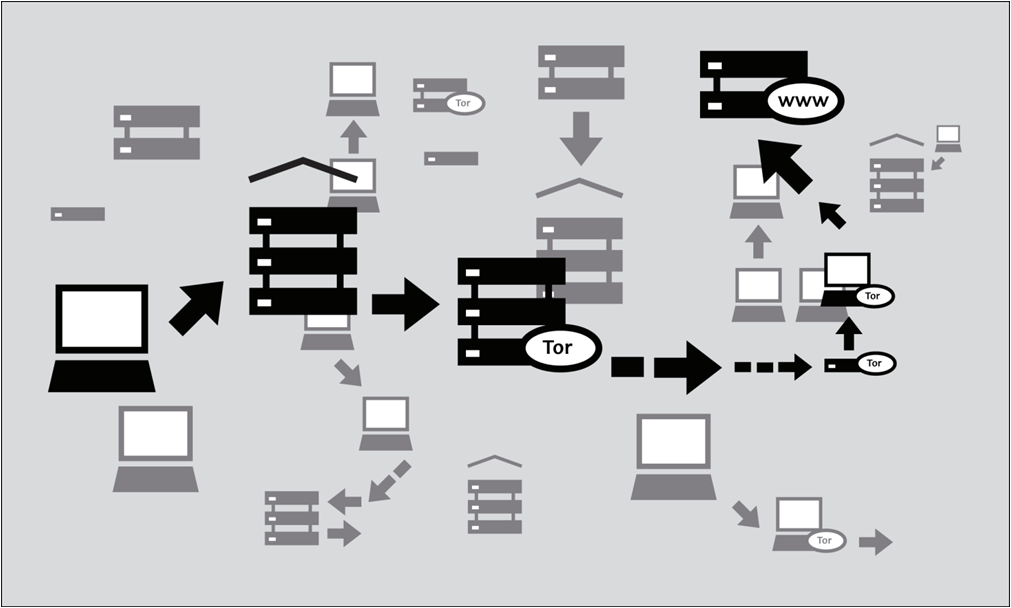
If you’re one of those who do a lot of things online using a mobile device, you should be concerned about Internet security. The virtual private network (VPN) is a…
Read More
More than 20 years ago, Bill Gates asserted that “content is king.” Most probably, he couldn’t predict back then how much content the readers would consume on the internet today….
Read More
Security analytics is a process of collecting data, aggregating, and using tools to analyze the data in order to monitor and identify threats. Depending on the tools being used, this…
Read More
The Principle of Least Privilege, or POLP, is the idea that any user, program, or even process should only be provided the bare minimum of privilege for them to perform…
Read More