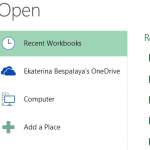
If your Excel file was left unsaved by accident, don’t fret – Microsoft understands mistakes happen and provides built-in...
Read MoreAuthor Details
-

Paul Hamilton259 Posts
If you suspect someone has blocked you on Facebook, various methods exist to investigate their actions. One option would...
Read MoreiCloud can be an easy and secure way to back up photos and videos, but accessing those files across...
Read MoreIf the iPhone force restart does not work as intended, there may be an issue with the iOS system....
Read MoreIf the YouTube app on your iPhone is crashing or will not open, there are various fixes you can...
Read MoreInstagram is an amazing social platform where you can stay in touch with your friends and influencers, but sometimes...
Read MoreAn inactive Facebook business page won’t do your brand any good; sometimes, it may be best to delete it...
Read MoreGet a simple solution for the question “Do AirPods Work With Android” – Yes, AirPods work well with Android,...
Read More