You Need to Know About The Bitcoin Double-Spending Exploit Against Tether Exchange

Tether, a U.S.-based cryptocurrency exchange with trading code “USDT” has been discovered to have a nasty loophole enabling a “double-spend” exploit. In cryptocurrency language, this happens when a certain number of Bitcoin or other digital currency covertly makes two or more deposit transactions using Blockchain technology. This effectively doubles the spending power of a certain amount of Bitcoin at one end and the 50% loss of Bitcoin value on the other end. The Bitcoin trading community has been recently warned to be on high alert and carefully scrutinize their transactions on the cryptocurrency exchange.
The news of the double-spending vulnerability has been released by SlowMist, a Chinese cybersecurity company specializing in cryptocurrency, via their twitter announcement dated June 28, 2018. https://t.co/EPzZIsZFzH
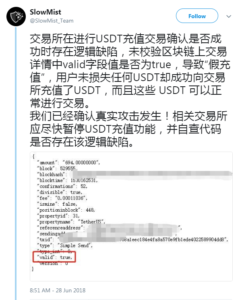
It was later clarified that the cause of the problem was a poorly handled transaction system of Tether. The individual making the deposit can transfer a certain number of Bitcoins to the mentioned Bitcoin exchange, even if the former has no Bitcoin balance at all. A bug in the JSON-RPC API is responsible for confirming a non-balance transaction as still valid, a fact pointed out by the SlowMist tweet shown above.
In a normal scenario, the depositor should receive a “not enough balance” error message after attempting to deposit a certain amount of Bitcoin to a currency exchange system—because they do not have the necessary funds to make a valid transaction. But due to this bug, the exchange system continues to recognize and confirm the completion of the deposit, even if no actual Bitcoin has entered the exchange system.
This is a serious situation and can be easily compared to a real-life banking incident where a depositor’s account is credited with a certain amount money, even though no actual currency was submitted. This is known in the cryptocurrency traders as “pretend value.”
The Tether asset platform, Omnilayer, posted this reply on Reddit: “I designed Omni so that to double-spend an Omni asset, you would have to double-spend Bitcoin. If I’m translating this correctly, it appears that what happened here is that an exchange wasn’t checking the valid flag on transactions. They accepted a transaction with valid=false (which they should not have), and then the second “double spend” transaction had valid=true, which they also accepted. Unless I am missing something, this is just poor exchange integration.”
The writer further explains, “This is in no protocol vulnerability, but rather a poor handling of incoming token payments, if this was indeed exploited in the wild. As far as we know, there was an integrator, which hasn’t checked the valid flag at all and simply credited the tokens, without ensuring and checking, whether they were actually transferred.”
The statement is understandable, as OmniLayer has a legal reason to protect its reputation and the name of Tether. As a cryptocurrency exchange site, Tether depends on the level of trust they enjoy from the cryptocurrency traders. And a loss of this trust means the end of their business in the crypto trading industry.
Upon this writing, the investigation is still ongoing. This incident may lead traders to doubt the reliability of using Tether as their cryptocurrency exchange in the future. All traders are expected to do their homework and study the reliability of the currency exchange they plan to use.
Some takeaways:
- No other exchange site was affected; this issue is isolated within Tether. The question of whether the actual OmniLayer provider was directly responsible is still open.
- OmniLayer confirms the double-spend, but they claim no liability to it.
- The Chinese cybersecurity company, SlowMist, has no record of fabrication and appears to be conducting legitimate cybersecurity consulting.
- Don’t believe what the social media commentators say, as many of those platforms are also traders making wild speculations.
- It is unknown how many traders took advantage of the bug and earned a lot of Bitcoin in the process. No one has come out to confess their part in the exploited bug or to earn more Bitcoins until the announcement of the bug by SlowMist.