Inside SamSam Ransomware’s $6 Million Ransom Profit

Ransomware is a big business for cybercriminals. In the age when the market is flooded by many competing cloud-storage and cloud-backup services, a significant number of them are even free – having a reliable backup in the enterprise is still lacking. Sophos, a mainstream antivirus firm has revealed it their report that SamSam ransomware’s authors have potentially earned almost $6 million worth of ransom payment.
“Most ransomware is spread in large, noisy and untargeted spam campaigns sent to thousands, or even hundreds of thousands, of people. They use simple techniques to infect victims and aim to raise money through large numbers of relatively small ransoms of perhaps a few hundred dollars each. SamSam is very different – it’s used in targeted attacks by a skilled team or individual who breaks into a victim’s network, surveils it and then runs the malware manually. The attacks are tailored to cause maximum damage and ransom demands are measured in the tens of thousands of dollars,” said the report.
Touted as the spiritual successor of WannaCry, SamSam is designed not as a run-of-the-mill ransomware with random targets, but something of its own category with maximizing profits as its main goal. This is done through extensive background research of the malware authors of the potential victims, before launching the SamSam attack through phishing or malicious links. As of this writing, the three most commonly attacked industries are the education, healthcare and government sectors, three industries which have the lowest cybersecurity defense investment.
“SamSam is actually deployed to computers on the victim’s network in the same way, and with the same tools, as legitimate software applications. Based on the known victims, it’s been widely speculated until now that SamSam attacks are directed specifically at the healthcare, government and education sectors. Sophos can reveal that this is not the case. The money trail also revealed that SamSam has netted nearly $6 million in ransom payments – about six times more than the most recent best estimate.” the report emphasized.
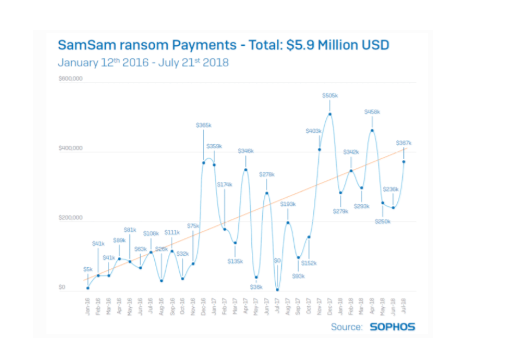
The graph above from Sophos further tracks the profitability levels of the SamSam ransomware. With the graph alone, it shows that the developers of the ransomware are making tons of money encrypting the victims’ data, lost data that can easily be restored in good condition if a good backup strategy is implemented.
SamSam relies on phishing and social engineering to spread itself in the network. A detailed analysis of the ransomware failed to show the presence of a worm-like behavior or module in the malware.
“If the SamSam attacker is on your network they will likely stay on it until they succeed unless they’re kicked off. Having gained access to a network, the SamSam operator uses a variety of tools to escalate their privileges to the level of Domain Admin. Then they scan the network for valuable targets and deploy and execute the malware as any self-respecting sysadmin might, using utilities such as PsExec or PaExec. Once it has been spread far and wide, the many copies of the ransomware are triggered centrally, starting within seconds of each other. On each infected machine, files are encrypted in a way that’s designed to cause the most damage in the shortest time,” the report concludes.