What Is a Security Operations Center (SOC)?
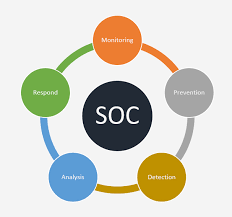
A Security Operations Center (SOC) specializes in monitoring and analyzing data to detect cyber threats and prevent attacks from them. They work to sort actual threats from false positives before triaging them according to severity.
Investigators also investigate and analyze incidents to ascertain their causes, such as identifying technical vulnerabilities that hackers exploited for attacks in the future. Such information can help avoid similar attacks in future.
Key Functions of a SOC
SOCs (Security Operations Centers) serve multiple functions. Their primary responsibility lies in monitoring, investigating and responding to security incidents; while also performing preventive activities such as vulnerability assessments, testing regimens and patching. Their teams use information gleaned from these activities to develop better cybersecurity processes, policies and tools within an organization.
A SOC must also be capable of recognizing and prioritizing threats according to their level of severity, using threat intelligence platforms that provide visibility across endpoints, networks, and clouds within an organization. Furthermore, automated tools must be available that reduce analysis time while providing faster alert response.
SOCs must also have systems in place to monitor compliance considerations dictated by industry regulations such as GDPR, HIPAA or PCI DSS to safeguard organizations against data breaches and potential fines. Furthermore, auditing and reporting processes must also be implemented within their SOC in order to guarantee adherence with security standards.
Key Tools Used in a SOC
An effective SOC requires various tools in order to effectively defend networks and data against advanced cyber threats. These may include SIEM/XDR systems, vulnerability management solutions, and threat intelligence platforms.
SOC teams need to regularly update their tool sets in order to stay ahead of sophisticated attacks, yet due to a global cybersecurity skills gap it may be challenging for SOCs to keep pace with ever-evolving hackers and their ever-evolving tools.
Additionally, SOCs must remain compliant with security standards imposed by industry and regulatory bodies like GDPR, HIPAA and PCI DSS to protect sensitive information while also avoiding fines and reputational damage associated with violating regulatory standards.
SOCs must also monitor vulnerabilities in their networks, alert IT teams and follow up with them afterwards to see if the issue was fixed. This can be an inefficient process without an automated solution that streamlines TDIR. Xcitium XDR eliminates manual tool pivoting by consolidating multiple security tools onto one platform.
SIEM
To effectively protect systems and data, a SOC needs to remain aware of any threats that could impact it. To achieve this goal, they must keep up-to-date with security innovations while possessing in-depth knowledge about endpoints, servers, perimeter devices and cloud resources as they function.
SOCs serve a vital function by monitoring the activity of these assets and alerting their team when anomalies are found. This process involves interpreting CTI threat feeds and log files from all company systems including applications, hardware, software and networks.
A SOC must also be capable of filtering out false positive alerts that clog up team time, which requires having an automated security solution with prepackaged TDIR use cases and prescriptive workflows that automate this process and reduce manual analysis required per alert. In turn, this allows SOC teams to focus their attention on more pressing issues related to cyber attacks; such as shutting down systems that have been compromised, terminating harmful processes, deleting files or taking other necessary actions against cyber threats such as shutting them off temporarily or isolating systems from cyber threats; such actions include shutting down/isolating affected systems, terminating harmful processes or even delete files depending on circumstances.
XDR
A Security Operations Center (SOC) safeguards an organization’s critical systems and data. This includes protecting everything within their networks such as servers, applications and endpoints used to connect customers as well as cloud resources or Internet-of-Things (IoT) devices that could pose risks.
To achieve this goal, the SOC relies on security tools that detect and investigate suspicious behavior, such as security information and event management (SIEM), endpoint detection and response (EDR) systems, and threat intelligence platforms. Many of these tools leverage machine learning technology to filter, parse, aggregate, and correlate data so the team is only alerted about relevant and dangerous incidents.
SOC teams also maintain logs to monitor activity and communications throughout an organization, which may reveal anomalies indicative of an attack and help the SOC team respond swiftly and efficiently.
To achieve this goal, the SOC regularly conducts vulnerability and penetration tests as well as updating application portfolio, security policies, and best practices accordingly. Furthermore, they stay informed about new threats by regularly reviewing security solutions, technologies, and industry news.
SOAR
When security threats are detected, SOC teams serve as the first responders. Acting quickly to address issues quickly by taking measures such as isolating endpoints, terminating harmful processes or deleting files to limit damage while protecting customers and employees’ private information, these teams work quickly to address any threats as soon as they arise.
The SOC team also conducts regular testing to identify weaknesses in an organization’s security systems, and reviews threat intelligence gathered from public, industry and dark web sources about cyberattacks, hackers and their threats gathered through regular news updates, threat assessments and reviews of news feeds from cybersecurity-related websites and publications. They then use this intelligence to update and modify security monitoring tools, policies, best practices and incident response plans accordingly.
SOC teams can streamline investigations and responses using software solutions like XDR to speed up analysis of potential cybersecurity incidents. These tools automate and standardize processes such as status checking, decision-making workflows, audits and enforcement actions to reduce response times while decreasing false alarms to keep analysts focused on real threats rather than false alarms.
Firewalls and IDS or IPS
A Security Operations Center’s primary purpose is to safeguard devices, applications and processes it protects. In order to do this effectively, it must possess an in-depth knowledge of all tools available at its disposal; similar to how carpenters must know which hammer will best drive nails but also how it should be swing; similarly a SOC must know how best to utilize its resources to their fullest extent.
This includes making sure the organization’s security solutions are up-to-date, performing routine maintenance on them, and developing backup policies and procedures in case of an incident. Furthermore, SOCs must also detect anomalies in network traffic, data and endpoints – these must then be triaged so as to not waste teams’ time on unimportant alerts or miss real threats altogether.
SOCs must keep pace with evolving threats by conducting vulnerability assessments and analyzing threat intelligence to spot new attack patterns or methods hackers use. Furthermore, incident responses include shutting down compromised systems, redirecting networks, resetting passwords or stopping compromised activities as quickly as possible – as well as conducting in-depth root cause analyses and documenting all actions taken against these incidents.
Benefits of a SOC
SOC teams not only ensure an organization’s security tools and policies are current, but they also perform preventive maintenance such as creating system backups, installing patches and upgrades and developing incident response procedures in case of data breach or ransomware attack.
The Security Operations Center (SOC) plays an essential role in keeping track of emerging threats and vulnerabilities by gathering threat intelligence from around the global network and acting upon any updates they discover. This is especially crucial because sophisticated actors often manage to evade conventional detection mechanisms like signature, rules and threshold-based solutions.
In case of an attack, a Security Operations Center acts as the initial line of defense by performing actions like shutting down or isolating endpoints, terminating harmful processes, deleting files and more with minimal impact to business operations. A SOC also ensures full visibility across all endpoints, servers and software within their organization to make sure there are no blind spots which attackers could take advantage of by monitoring all aspects of endpoints, servers and software in real-time – eliminating blind spots which attackers might exploit by monitoring them all.
Conclusion
Businesses operating in industries with strict regulations such as healthcare, finance, insurance, and banking must often abide by stringent regulations. As these industries generate large quantities of data that are vulnerable to cybercrime attacks without an SOC team in place. Threat actors could easily exploit existing vulnerabilities by exploiting existing vulnerabilities to attack these businesses.
One of the primary purposes of a SOC is to develop an intimate knowledge of all hardware, software and tools used in an organization’s network. Through monitoring this data, SOC teams can detect threats as soon as anomalies or abnormal trends appear in this data set.
SOCs serve a vital purpose by continuously optimizing their protections. This may involve anything from tweaking a threat detection database to creating systems to leverage cyber intelligence available. The most efficient SOCs stay up-to-date with these resources and implement updates quickly – this ensures their teams have everything necessary to protect against novel threats quickly while staying ahead of cybercriminals and mitigating the impact of incidents when they do happen.