Tor Deep Web Search Engine – How to Download & use Tor Onion Browser Sites Safely (2018 Edition)
What is Tor?
Tor is a free, open-source browser that functions using the onion routing process. Tor works on all kinds of internet protocols- HTTP, HTTPS, FTP, Gopher etc.
The most notable thing about the Tor browser is that it provides secure browsing by creating an encrypted environment from where no one can access the users’ data or even see it. Tor, which facilitates secure, anonymous browsing helps access the deep web and is above and beyond all network surveillance, footprint tracking, traffic analysis etc. It secures you from malware as well.
How to Use the Tor Browser?
You should begin by downloading the installer. ( For Windows, Mac & Linux)
Installation Instruction Onion Browser on MAC:
i. Download above Mac installer & same on your local folder
ii. This take you to opens the .dmg file.
iii. Now, drag the included file into your Applications folder
iv. Tor Onion Browser App ask you to choose your language.
That’s it, you have installed your Tor browser on MAC PC.
Installation Instruction Onion Browser on Linux:
i. Download above LINUX installer & same on your local folder
ii. Extract the package and type the below comment
For 64-bit version
tar -xvJf tor-browser-linux64-7.0.11_LANG.tar.xz
For 32-bit version
tar -xvJf tor-browser-linux32-7.0.11_LANG.tar.xz
iii. After completing the above process, switch the directory to Tor browser by using the below comment
cd tor-browser_LANG
iv. To run Tor Browser click, Tor Browser Setup icon & it will launch Firefox.
Installation Instruction Onion Browser on Windows:
i. Download Above Windows installer
ii. Double click to Run
iii. Select your language & click OK (Note* You must have 80MB Free disk space)
iv. Click Install
Ensure you have the proper version of the browser, then install the software. For Windows, it’s like installing any other software since Tor comes as an EXE file for Windows. (Tor Versions)
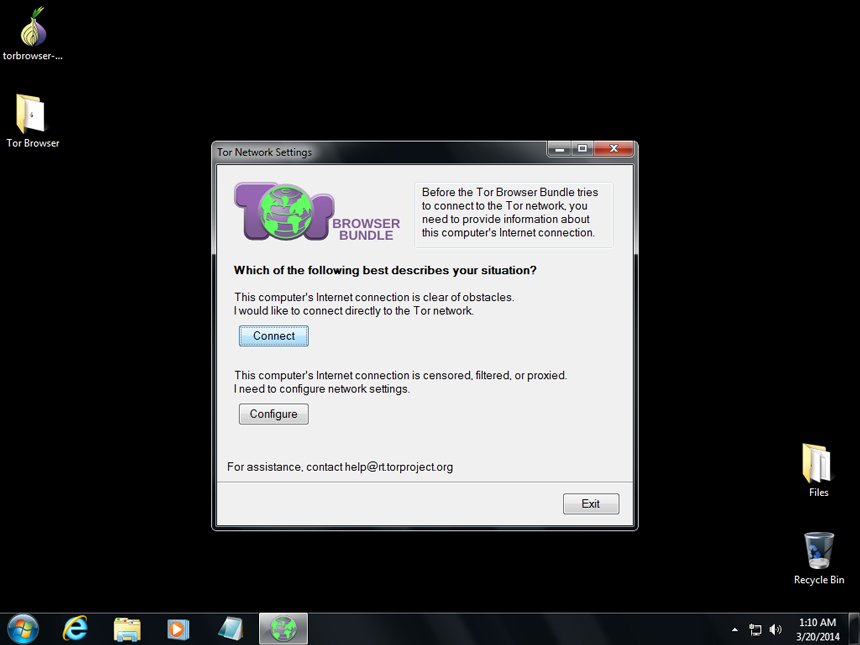
Once installed, you’d find a folder named ‘Tor Browser’. Open the folder, you’d find ‘Start Tor Browser.exe’. Click on that…
A new window opens. You’d be asked if you’d like to connect directly to the Tor network or configure proxy settings first. The direct option is the best.
Choose to connect directly. A version of Firefox will launch.
You’re connected to the Tor network. Enjoy anonymous browsing!!! You can confirm by going to whatsmyip. com; if your browser shows you coming from a different location, you’re on to anonymous browsing.
How to Access Tor Safely?
Tor provides secure, anonymous browsing. Thus neither your ISP nor the government is able to view your online activity. But it’s evident to them that you are on Tor and that could cause issues. For example, in the U.S, the FBI can search or seize any computer simply because of Tor usage. Experts would often advise using Tor with another layer of security, via a VPN (Virtual Private Network).
Using a VPN allows encryption of all internet traffic traveling to and from a system/device, thus giving anonymity plus privacy. Connect to your VPN and then fire up Tor Browser, you’re using Tor over VPN. Your ISP would see that you are using an encrypted VPN traffic, but wouldn’t know you are on Tor. The VPN provider also cannot see the content of your encrypted Tor traffic. It’s always advisable to use a logless VPN, which wouldn’t store any traffic logs or session logs.
To be remembered is the fact that Tor over VPN doesn’t protect you from malicious Tor exit nodes, which could decrypt your traffic and steal personal data or inject malware. This can be solved by using VPN over Tor. VPN over Tor would protect you from the bad exit nodes, but the disadvantage is that your ISP would know that you’re using Tor.
Who uses Tor? What are the Benefits?
The Tor Browser is compatible with different kinds of devices- you can use the Android version of the Mac version too, depending on the kind of device used.
Different kinds of people use the Tor Search Engine, based on the different kinds of benefits it provides. Here’s a look at the different kinds of people using it, plus the benefits it bestows on them-
Journalists and activists- They use the browser to file their reports and to expose people. They use the browser to bring out cases of corruption, injustice etc. This is because of the anonymity that Tor provides.
Parents- Parents can use Tor browser to help their children use the internet in anonymity, without revealing their identity. This is for the security of the kids.
Corporates and professionals- Corporate entities use Thor for maintaining confidentiality, especially while sharing confidential documents which need to be protected from third parties. Professionals and corporates use Thor to hide browsing history- professionals from their employers and corporates from internet providers who could use the history for marketing purposes.
The Military- The military uses Thor for information gathering. It’s also used to shield identities of undercover agents and to provide them secret online communication.