Seqrite Threat Report; The Threat That is Likely to Continue in 2019
With a population of 1.36 billion as of United Nations’ 2018 estimate, India is a big market in computers and electronic gadgets. This level of penetration of computing promotes a healthy level of BYOD (Bring Your Own Devices) in India based firms, as more employees want to use their own gadgets for their professional tasks. With just its size, the number of India’s workforce including their gadgets outnumber total population of even the United States, European Union or Russia, which means more potential targets for cyber attacks.
Seqrite, an enterprise security consulting firm, released their latest Threat Report for the 3rd Quarter of 2018. Detailing the cyber threats that India faced for the last three months, with worms, unpatched vulnerabilities in software and ransomware as the most common cases. It is also the first edition of the threat report which mentioned the intricate growth of cryptojacking incidents, where the infected machines silently mine cryptocurrency without their users detecting it. In just one day, Seqrite claims there is 24,000 crytojacking incidents in India for the 3rd Quarter of 2018 alone.
“There is no denying that enterprises face an unparalleled security challenge today. Growing interconnectivity has demolished traditional security perimeters. Every endpoint, every node, every device connected to enterprise networks has become a point of entry for attackers looking to steal invaluable information and disrupt business operations. Attacks are becoming smarter and more targeted, and are causing much greater damage. In this context, the Seqrite Quarterly Threat Report Q3 2018 serves to underline the sheer scale of risk that Indian organisations are exposed to, at present,” explained Sanjay Katkar, CTO of Quick Heal Technologies, a partner of Seqrite in the compilation of the report.
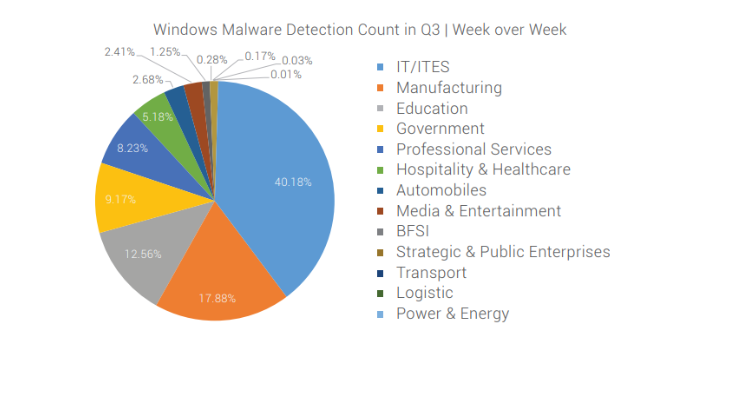 Above is the pie chart of the detection rate that Seqrite detected for the 3rd quarter of 2018, with IT and manufacturing sector occupies the majority target of exposures and cybersecurity threats. In each industry mentioned in the pie graph, there is a list of top malware that are most commonly detected.
Above is the pie chart of the detection rate that Seqrite detected for the 3rd quarter of 2018, with IT and manufacturing sector occupies the majority target of exposures and cybersecurity threats. In each industry mentioned in the pie graph, there is a list of top malware that are most commonly detected.
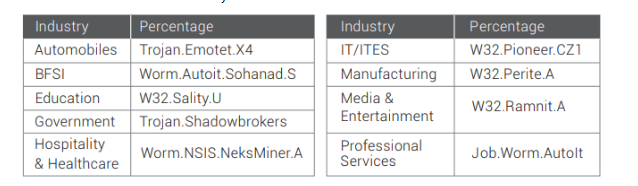
This proves the hypothesis that some malware is specifically developed to focus on a particular industry, some for the victim to experience heavy financial damage, while others for espionage purpose.
Just like the previous quarterly report, the Q3 report also published the top 10 malware detected across industries. This gives a snapshot of the most successful malware, as it takes a lot of effort to develop something that will thrive, even in the presence of real-time virus scanners:
- W32.Sality.U
- W32.Pioneer.CZ1
- Trojan.Starter.YY4
- VBS.Dropper.A
- W32.Ramnit.A
- Worm.AUTOIT.Tupym.A
- Trojan.Emotet.X4
- LNK.Cmd.Exploit.F
- W32.Brontok.Q
- W32.Perite.A
Although not dangerous, Seqrite also publishes the quarter’s most commonly detected PUA (Potentially Unwanted Applications).
- PUA.Conduitltd.Gen
- PUA.Auslogicsl.Gen
- PUA.Opencandyi.Gen
- PUA.Greentreea.Gen
- PUA.Mindsparki.Gen
- PUA.Conduitltd2.Gen
- PUA.Sweetimtec.Gen
- PUA.Mindsparki1.Gen
- PUA.Somotoltd.Gen
- PUA.Conduitltd1.Gen
These apps normally hide from the users by piggybacking in the installation of a typical app, like Flash Player or Adobe PDF Reader. They install themselves in the system, as the user typically just clicks next, next and next in the installation wizard for utility programs such as Flash or PDF reader.
The bottom line, 2019 is expected to be the continuation of the years preceding it. There is no single solution to the cybersecurity issues people are facing, whether in India or for the rest of the world. A kind of mixed strategy needs to be adapted by IT teams across the board in order to maintain a credible cybersecurity defense while not breaking the bank.