Most people who use PCs will be connected to the Internet, in fact, almost everyone has a smartphone, the most personal of all personal computers. This means that many are…
Read More
A typical antivirus products and End Point services today generally speaking comes with two ways of detecting malware: Signature-based Heuristics The signature-based antivirus has evolved since the days of the…
Read More
ASUS, the leading manufacturer of computers suffered a cyberattack that allowed hackers to infect malware to more than 50,000 customers. The hacker after breaking the Taiwan-based tech company’s server, made…
Read More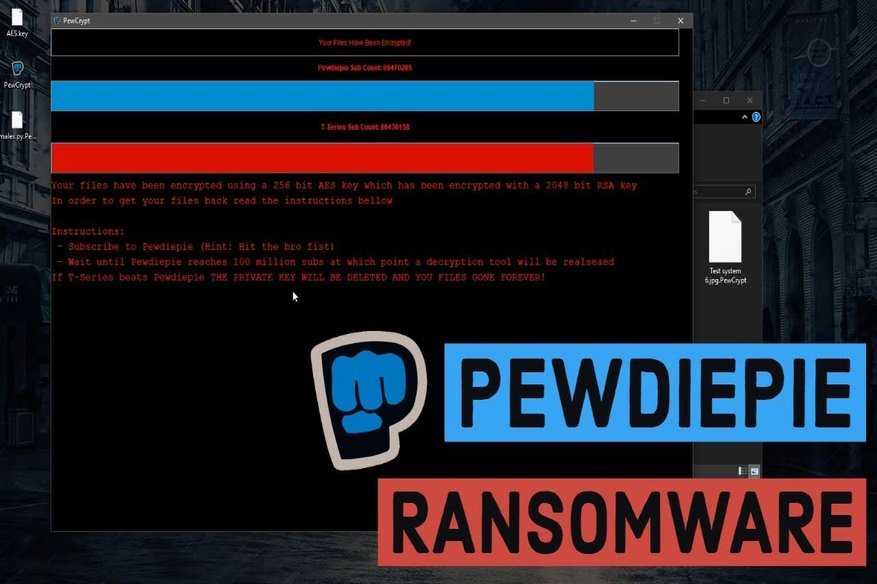
Obsession really goes a long way for people to get out of their way to cause trouble for others. As PewDiePie emerges as a Youtube sensation, his fanbase grew to…
Read More
According to a blog post from threat research department Unit 42 of cyber security company Palo Alto Networks published on March 19, an upgraded cardinal RAT malware targets Israeli fintech…
Read More
We have always been stating that for any enterprise, security is not just about solutions and the technical aspects, it includes the human element as well. Every single employee who…
Read More
In a surprise move at the RSA security convention, the National Security Agency announced the release of Ghidra, a free open source free software engineering toolkit. NSA has been using…
Read More
Mimecast has released its newest Email Security Risk Assessment Quarterly Report (ESRA) for the first quarter of 2019, which can be summarized in one phrase: “nothing is new.” The overused…
Read More
When it comes to malware development and infection campaigns, it does not matter where the vulnerable computer systems are located. Malware in the wild are not limiting themselves to just…
Read More
If you are working as a security professional and interested in this specific field of knowledge, you must be known these top 10 Linux distro that suits your purpose. Remember…
Read More
